-
-Network-wide ad blocking via your own Linux hardware
+
+ 
+ Network-wide ad blocking via your own Linux hardware
--
-
-
- Frequently Asked Questions -
- Pi-hole Wiki -
- Feature Requests -
- Discourse User Forum -
- Gitter (Real-time chat) -
- YouTube -
 +### [Faster-than-light Engine](https://github.com/pi-hole/ftl)
+
+[FTLDNS](https://github.com/pi-hole/ftl) is a lightweight, purpose-built daemon used to provide statistics needed for the Web Interface, and its API can be easily integrated into your own projects. As the name implies, FTLDNS does this all *very quickly*!
+
+Some of the statistics you can integrate include:
+
+- Total number of domains being blocked
+- Total number of DNS queries today
+- Total number of ads blocked today
+- Percentage of ads blocked
+- Unique domains
+- Queries forwarded (to your chosen upstream DNS server)
+- Queries cached
+- Unique clients
+
+The API can be accessed via [`telnet`](https://github.com/pi-hole/FTL), the Web (`admin/api.php`) and Command Line (`pihole -c -j`). You can find out [more details over here](https://discourse.pi-hole.net/t/pi-hole-api/1863).
+
+### The Command Line Interface
+
+The [pihole](https://docs.pi-hole.net/core/pihole-command/) command has all the functionality necessary to be able to fully administer the Pi-hole, without the need of the Web Interface. It's fast, user-friendly, and auditable by anyone with an understanding of `bash`.
Some notable features include:
-* [Whitelisting, Blacklisting and Wildcards](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#whitelisting-blacklisting-and-wildcards)
-* [Debugging utility](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#debugger)
-* [Viewing the live log file](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#tail)
-* [Real-time Statistics via `ssh`](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#chronometer) or [your TFT LCD screen](http://www.amazon.com/exec/obidos/ASIN/B00ID39LM4/pihole09-20)
-* [Updating Ad Lists](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#gravity)
-* [Querying Ad Lists for blocked domains](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#query)
-* [Enabling and Disabling Pi-hole](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#enable--disable)
-* ... and *many* more!
-You can read our [Core Feature Breakdown](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown), as well as read up on [example usage](https://discourse.pi-hole.net/t/the-pihole-command-with-examples/738) for more information.
+- [Whitelisting, Blacklisting and Regex](https://docs.pi-hole.net/core/pihole-command/#whitelisting-blacklisting-and-regex)
+- [Debugging utility](https://docs.pi-hole.net/core/pihole-command/#debugger)
+- [Viewing the live log file](https://docs.pi-hole.net/core/pihole-command/#tail)
+- [Updating Ad Lists](https://docs.pi-hole.net/core/pihole-command/#gravity)
+- [Querying Ad Lists for blocked domains](https://docs.pi-hole.net/core/pihole-command/#query)
+- [Enabling and Disabling Pi-hole](https://docs.pi-hole.net/core/pihole-command/#enable-disable)
+- ... and *many* more!
+
+You can read our [Core Feature Breakdown](https://docs.pi-hole.net/core/pihole-command/#pi-hole-core) for more information.
### The Web Interface Dashboard
+
This [optional dashboard](https://github.com/pi-hole/AdminLTE) allows you to view stats, change settings, and configure your Pi-hole. It's the power of the Command Line Interface, with none of the learning curve!
-
+### [Faster-than-light Engine](https://github.com/pi-hole/ftl)
+
+[FTLDNS](https://github.com/pi-hole/ftl) is a lightweight, purpose-built daemon used to provide statistics needed for the Web Interface, and its API can be easily integrated into your own projects. As the name implies, FTLDNS does this all *very quickly*!
+
+Some of the statistics you can integrate include:
+
+- Total number of domains being blocked
+- Total number of DNS queries today
+- Total number of ads blocked today
+- Percentage of ads blocked
+- Unique domains
+- Queries forwarded (to your chosen upstream DNS server)
+- Queries cached
+- Unique clients
+
+The API can be accessed via [`telnet`](https://github.com/pi-hole/FTL), the Web (`admin/api.php`) and Command Line (`pihole -c -j`). You can find out [more details over here](https://discourse.pi-hole.net/t/pi-hole-api/1863).
+
+### The Command Line Interface
+
+The [pihole](https://docs.pi-hole.net/core/pihole-command/) command has all the functionality necessary to be able to fully administer the Pi-hole, without the need of the Web Interface. It's fast, user-friendly, and auditable by anyone with an understanding of `bash`.
Some notable features include:
-* [Whitelisting, Blacklisting and Wildcards](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#whitelisting-blacklisting-and-wildcards)
-* [Debugging utility](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#debugger)
-* [Viewing the live log file](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#tail)
-* [Real-time Statistics via `ssh`](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#chronometer) or [your TFT LCD screen](http://www.amazon.com/exec/obidos/ASIN/B00ID39LM4/pihole09-20)
-* [Updating Ad Lists](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#gravity)
-* [Querying Ad Lists for blocked domains](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#query)
-* [Enabling and Disabling Pi-hole](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown#enable--disable)
-* ... and *many* more!
-You can read our [Core Feature Breakdown](https://github.com/pi-hole/pi-hole/wiki/Core-Function-Breakdown), as well as read up on [example usage](https://discourse.pi-hole.net/t/the-pihole-command-with-examples/738) for more information.
+- [Whitelisting, Blacklisting and Regex](https://docs.pi-hole.net/core/pihole-command/#whitelisting-blacklisting-and-regex)
+- [Debugging utility](https://docs.pi-hole.net/core/pihole-command/#debugger)
+- [Viewing the live log file](https://docs.pi-hole.net/core/pihole-command/#tail)
+- [Updating Ad Lists](https://docs.pi-hole.net/core/pihole-command/#gravity)
+- [Querying Ad Lists for blocked domains](https://docs.pi-hole.net/core/pihole-command/#query)
+- [Enabling and Disabling Pi-hole](https://docs.pi-hole.net/core/pihole-command/#enable-disable)
+- ... and *many* more!
+
+You can read our [Core Feature Breakdown](https://docs.pi-hole.net/core/pihole-command/#pi-hole-core) for more information.
### The Web Interface Dashboard
+
This [optional dashboard](https://github.com/pi-hole/AdminLTE) allows you to view stats, change settings, and configure your Pi-hole. It's the power of the Command Line Interface, with none of the learning curve!
-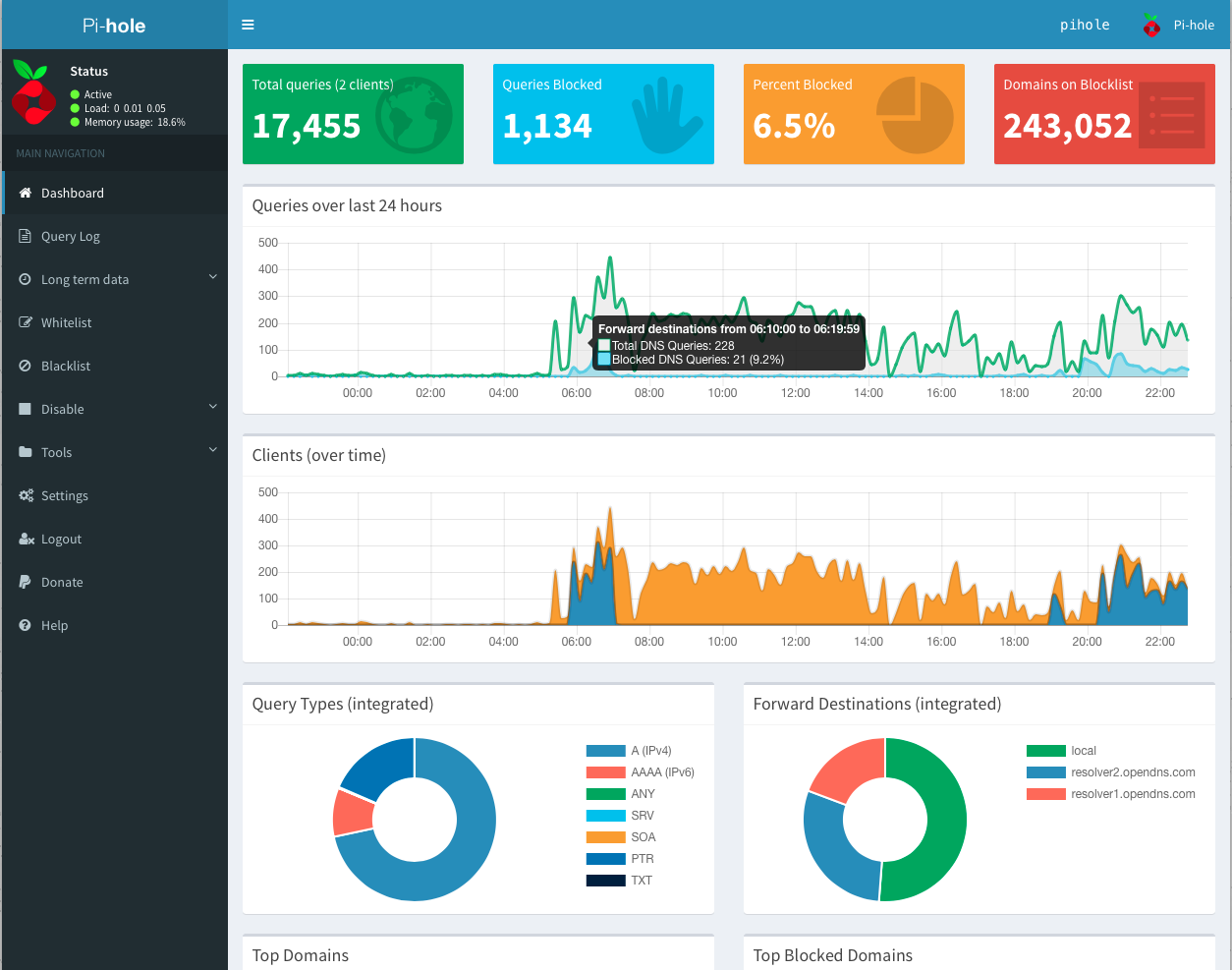 -
Some notable features include:
-* Mobile friendly interface
-* Password protection
-* Detailed graphs and doughnut charts
-* Top lists of domains and clients
-* A filterable and sortable query log
-* Long Term Statistics to view data over user-defined time ranges
-* The ability to easily manage and configure Pi-hole features
-* ... and all the main features of the Command Line Interface!
+
+- Mobile friendly interface
+- Password protection
+- Detailed graphs and doughnut charts
+- Top lists of domains and clients
+- A filterable and sortable query log
+- Long Term Statistics to view data over user-defined time ranges
+- The ability to easily manage and configure Pi-hole features
+- ... and all the main features of the Command Line Interface!
There are several ways to [access the dashboard](https://discourse.pi-hole.net/t/how-do-i-access-pi-holes-dashboard-admin-interface/3168):
-1. `http://
-
Some notable features include:
-* Mobile friendly interface
-* Password protection
-* Detailed graphs and doughnut charts
-* Top lists of domains and clients
-* A filterable and sortable query log
-* Long Term Statistics to view data over user-defined time ranges
-* The ability to easily manage and configure Pi-hole features
-* ... and all the main features of the Command Line Interface!
+
+- Mobile friendly interface
+- Password protection
+- Detailed graphs and doughnut charts
+- Top lists of domains and clients
+- A filterable and sortable query log
+- Long Term Statistics to view data over user-defined time ranges
+- The ability to easily manage and configure Pi-hole features
+- ... and all the main features of the Command Line Interface!
There are several ways to [access the dashboard](https://discourse.pi-hole.net/t/how-do-i-access-pi-holes-dashboard-admin-interface/3168):
-1. `http://
- Pi-hole: Your black hole for Internet advertisements
- Did you mean to go to the admin panel? - + // When directly browsing via IP or authorized hostname + // Render splash/landing page based off presence of $landPage file + // Unset variables so as to not be included in $landPage or $splashPage + unset($svPasswd, $svEmail, $authorizedHosts, $validExtTypes, $currentUrlExt); + // If $landPage file is present + if (is_file(getcwd()."/$landPage")) { + unset($serverName, $viewPort); // unset extra variables not to be included in $landpage + include $landPage; + exit(); + } + // If $landPage file was not present, Set Splash Page output + $splashPage = <<
 +
+